Cyber Defense Services
Needs-based and modular implementation
Selectable modules. A central platform for analysis, detection & response.
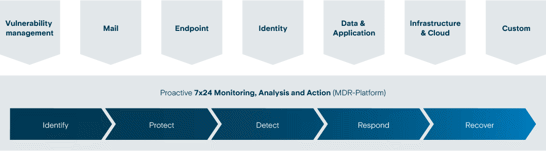
Vulnerability management (identify and close vulnerabilities)
Regularly scan for vulnerabilities (infrastructure and applications) and analyze the risks for the customer. Make specific recommendations and act directly if necessary.
Mail Security (protection of your email-inboxes)
Emails are still one of the most critical vectors for attacks. With this module we protect your email inbox (phishing, BEC, fraud, etc.)
Endpoint Security (endpoint protection)
The endpoint (whether desktop, notebook or server) is a central component of your organization. Proactive monitoring of the endpoint is central.
Identity Security (protection of identities)
Protecting digital identities is crucial in a global world. With this model we recognize whether identities have been stolen or misused (leaked & misused identities, password-spray or leveraging of MFA, etc.).
Data & Application Security (protection of files and cloud applications)
Fileservers, sharepoints, teams and other cloud-applications need adequate and proactive protection. DLP (Data Loss Prevention) is also part of this module.
Infrasturcture & Cloud Security (infrastructure and cloud protection)
Protection of your Azure infrastructure and the associated cloud-workloads.
Customer-specific requirements
Do you have your own in-house application that also needs to be monitored? Or onpremise components that need to be integrated? With this module we onboard individual requirements.
Bug Bounty as a Service
A continuous security test performed by certified ethical hackers — transparent, efficient, and affordable. Vulnerabilities are continuously identified, analyzed, and reported with actionable recommendations within 48 hours.
Benefits